Nothing on this page should be construed as legal advice. If you are concerned that your online information or communications are being used against you by the government, your employer, or other individuals, consult with an attorney for guidance.
For more in-depth information on online security, visit the Electronic Frontier Foundation’s Surveillance Self-Defense guide. There’s also the Digital Security Checklists for Activists, which has a page specifically for federal employees.
Privacy Basics
As a general rule, do not put anything in writing that could be used against you. That includes text messages, emails, and social media posts.
Be thoughtful about phone calls, video chats, and voicemails, as well. If you are uncertain about the security of any electronic communication, don’t say anything controversial or risky.
Keep handwritten notes at work rather than relying on electronic devices that your employer owns. This can include taking notes during meetings and calls that relate to your employment status or other sensitive work situations. If necessary, write down notes in private after meetings to preserve a contemporaneous record, even if you don’t feel comfortable doing so during meetings or calls.
Be cautious about discussing sensitive topics at work or any place where you might be overheard.
Credit Freezes
The three credit reporting agencies allow consumers to freeze their credit. This prevents new lenders from pulling your credit records, which means no one can open a credit account or take out a loan using your identity. Freezing credit is free. You will need to create an account at each credit agency and place each freeze separately.
Parents or caregivers can also freeze their children’s credit reports. This can be especially important for high school and college students whose FAFSA data might be at risk.
Here are links to each credit agency:
Secure Text Messaging and Emailing
To add a level of security to texting, consider using messaging apps that offer end-to-end encryption. Encrytpedmessages cannot be read by anyone else even if the messages are intercepted.SMS and traditional text messages do NOT have end-to-end encryption, so there is a possibility that the messages could be vulnerable to hacking or surveillance.
Messaging between iPhones does have end-to-end encryption, but that protection isn’t available when messaging people with Android phones or other devices.
Signal and WhatsApp both offer end-to-end encryption for messaging, voice, and video calls. WhatsApp is a Meta product, so it falls under the same corporate umbrella as Facebook and Instagram. Signal is supported by the Signal Foundation, a 501(c)3 non-profit dedicated to privacy in communication.
Everything You Need to Know About the Privacy-Focused Messaging App Signal – CNET
Why everyone should be using Signal instead of WhatsApp – Wired
Some email services like Proton Mail offer encryption for more communications. Full security measures may only be available when all parties are using the same platform for communicating. Even if you use an encrypted email service, the recipient’s email platform may be able to glean information about your location, ISP, and other metadata.
PC Mag has a list of secure email services.
Mobile Phone Security
Reviewing your phone’s security and privacy settings periodically is a smart practice. The Electronic Frontier Foundation has helpful guides on the privacy functions for both Apple and Android phones.
How to: Get to Know iPhone Privacy and Security Settings
How to: Get to Know Android Privacy and Security Settings
One important consideration is how you sign into your phone. It may be more secure to switch to a passcode to unlock your phone rather than face or fingerprint recognition. The Electronic Frontier Foundation explains:
In the United States, using a biometric—like your face scan or fingerprint—to unlock your phone may also compromise legal protections for the contents of your phone afforded to you under the Fifth Amendment privilege against compelled incrimination. Under current law—which is still in flux—using a memorized passcode generally provides a strongerlegal footing to push back against a court order of compelled device unlocking/decryption. While EFF continues to fight to strengthen our legal protections against compelling people to decrypt their devices, there is currently less protection against compelled face and fingerprint unlocking than there is against compelled password disclosure.
Protect Online Data
Secure passwords on all your online accounts can protect you from identity theft and other threats. Password managers are tools that can help you create and store secure passwords. Tools like NordPass or Proton Pass can assist with password management. PC Magazine has a list of recommended password managers for 2025.
Web browsers like Firefox or Brave and search engines like DuckDuckGo or Brave Search are more privacy-friendly than Google, which tracks all activity, shares it with third parties, and creates targeting search results. PC Magazine published reviews of various privacy-friendly browsing tools.
VPN and Network Security
Whenever possible, use your own private WiFi connection and check your router and network security settings regularly.
Consider using a VPN (Virtual Private Network), which creates a private encrypted connection to a server run by the VPN company. These are generally designed to be more secure than default internet connections, and can make your internet connection appear to come from another geographic location. Be thoughtful about choosing a VPN, since they can vary immensely based on the provider’s privacy and security stances. Some may be able to get around national firewalls- but again, they vast immensely, and all VPN companies need to track a certain amount of data about you to work. In general, free VPN services might help you watch anime not released in the US, but won’t help you from a privacy perspective; some of the more secure options include Mullvad, Mozilla, IVPN, . https://freedom.press/digisec/blog/choosing-a-vpn/
The Devil is in the (Metadata) Details
Be aware of how much metadata is being captured as you conduct activities online. Some companies, especially social media companies, harvest a great deal of metadata on your activities; websites drop cookies and read your IP location, browser and device type and more. These details can make it very possible to learn a great deal about a person. You can limit the amount of data you leave behind by choosing a browser that prevents sites from tracking you. DuckDuckGo and FireFox are both free browsers with strong privacy protections
Of particular note: Check your phone photography settings, especially what data is embedded or stripped when you send it. Photos may contain very specific location data, which can be visible if you send or post the images.
EXIF Removal Tools iOS (no apps required)
Tips and Tricks
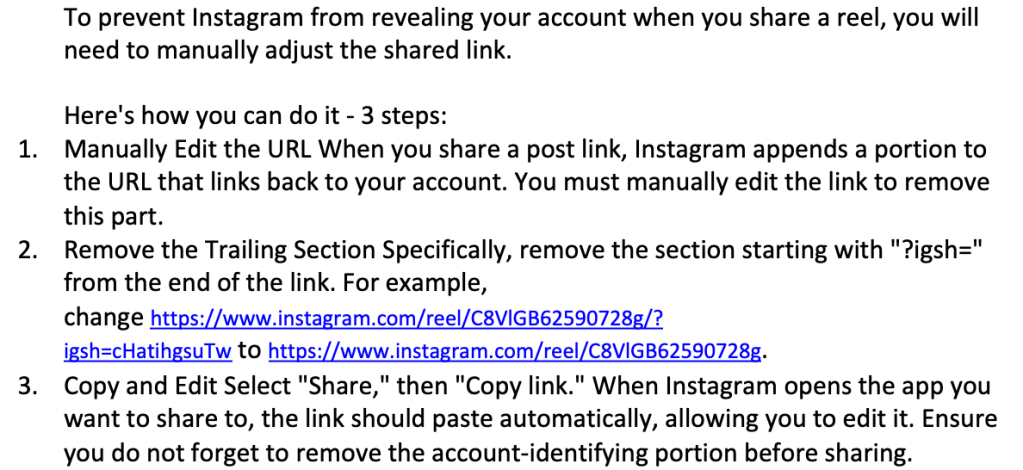
Other Resources


